TABLE OF CONTENTS
- Learn the Real Cost of Telecommunications Fraud
- The Primary Types of Telecommunications Hacking
- How Hackers Exploit Video to Perform SIP Toll Fraud
- Immediate Tactics to Prevent Telecommunications Network Hacking
- Advanced Tactics to Avoid Exploits in SIP Toll Fraud
- How to Discover and Take Action Against SIP Toll Fraud Probes with Vyopta
SUMMARY
Recently, an architecture firm based in Norcross, GA was surprised by a $166,000 phone bill they accrued in a single weekend. After days of research, the firm’s IT team found that hackers had placed premium-rate phone calls through their network from locations like Gambia, Somalia, and the Maldives. The firm found themselves owing their phone provider what would have taken them 34 years to accumulate based on their legitimate phone usage reports filed with the Federal Communications Commission.
This lack of awareness leaves many businesses falling victim to telecommunications fraud. IT teams are unable to produce the data required to prove charges are fraudulent or never notice the charges which go unnoticed and hidden in larger budgets.
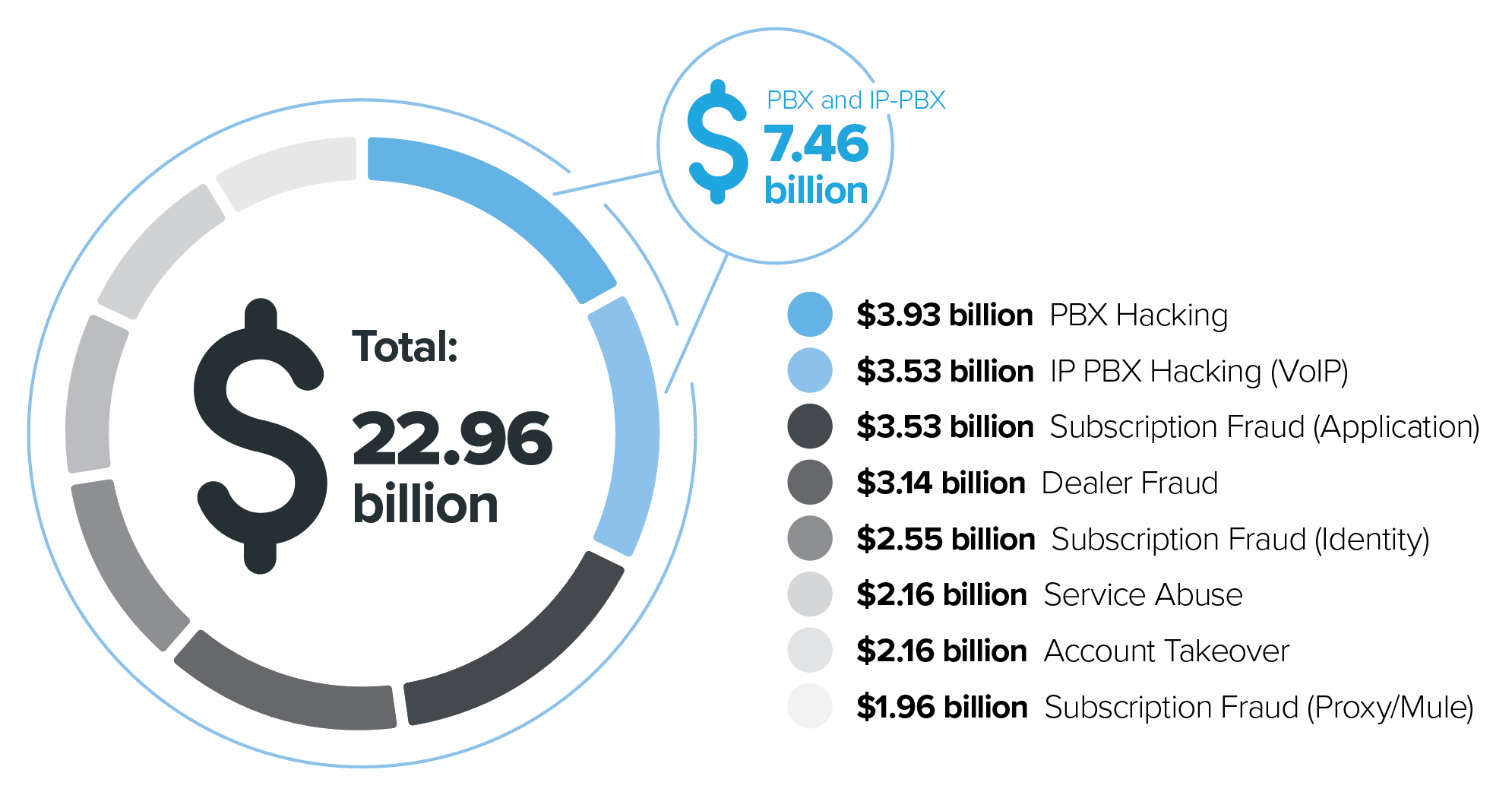
In fact, the Communications Fraud Control Association (CFCA), an industry organization on a mission to reduce fraud against carriers, conducts a bi-yearly Global Fraud Loss Survey. According to their latest survey the telecommunications industry experienced $38.1 billion in fraudulent charges in 2016. What is concerning is that we know cyber fraudsters are continuously working to develop new and unusual ways to siphon money from well-known, established organizations of all shapes and sizes. To the right, you’ll see the top fraud loss categories reported by operators in 2015 to the CFCA shook out:
To help, we’ve pulled together everything you need to explain the impact telecommunications fraud can have so you can get the right tools to protect your network, your brand, and your business’s bottom line.