According to the New York Times, an architecture firm based in Norcross, GA was recently surprised by a $166,000 phone bill they accrued in a single weekend. After days of research, the firm’s IT team found that hackers had placed premium-rate phone calls through their telecommunications network from locations like Gambia, Somalia, and the Maldives. The firm found themselves owing their phone provider what would have taken them 34 years to accumulate based on their legitimate phone usage reports filed with the Federal Communications Commission, a defining matter of telecommunication security issues.
Unfortunately, companies find themselves in similar situations quite frequently and often keep things under wraps to avoid negative press regarding security. This lack of awareness has created a vicious circle of vulnerability resulting in lawsuits with phone providers and internal friction between the financial and already overworked IT departments. Many businesses who fall victim to telecommunications security fraud either are unable to produce the evidence or data required to prove charges are fraudulent or never notice the charges which go unnoticed and hidden in larger budgets.
Ultimately though, the blame seems to fall squarely on the shoulders of the IT department. After all, network security is routinely their responsibility.
The reality is that telecommunications fraud (e.g., phone hacking, Session Initiation Protocol (SIP), and H.323 Toll Fraud via audio and video conferencing, etc.) is a multi-billion dollar threat organization’s cannot afford – no matter their size. We’ve pulled together everything you need to explain the impact telecommunications fraud can have on your organization, giving you the right tools to protect your network, your brand, and your business’s bottom line.
The Real Cost of Telecommunications Fraud
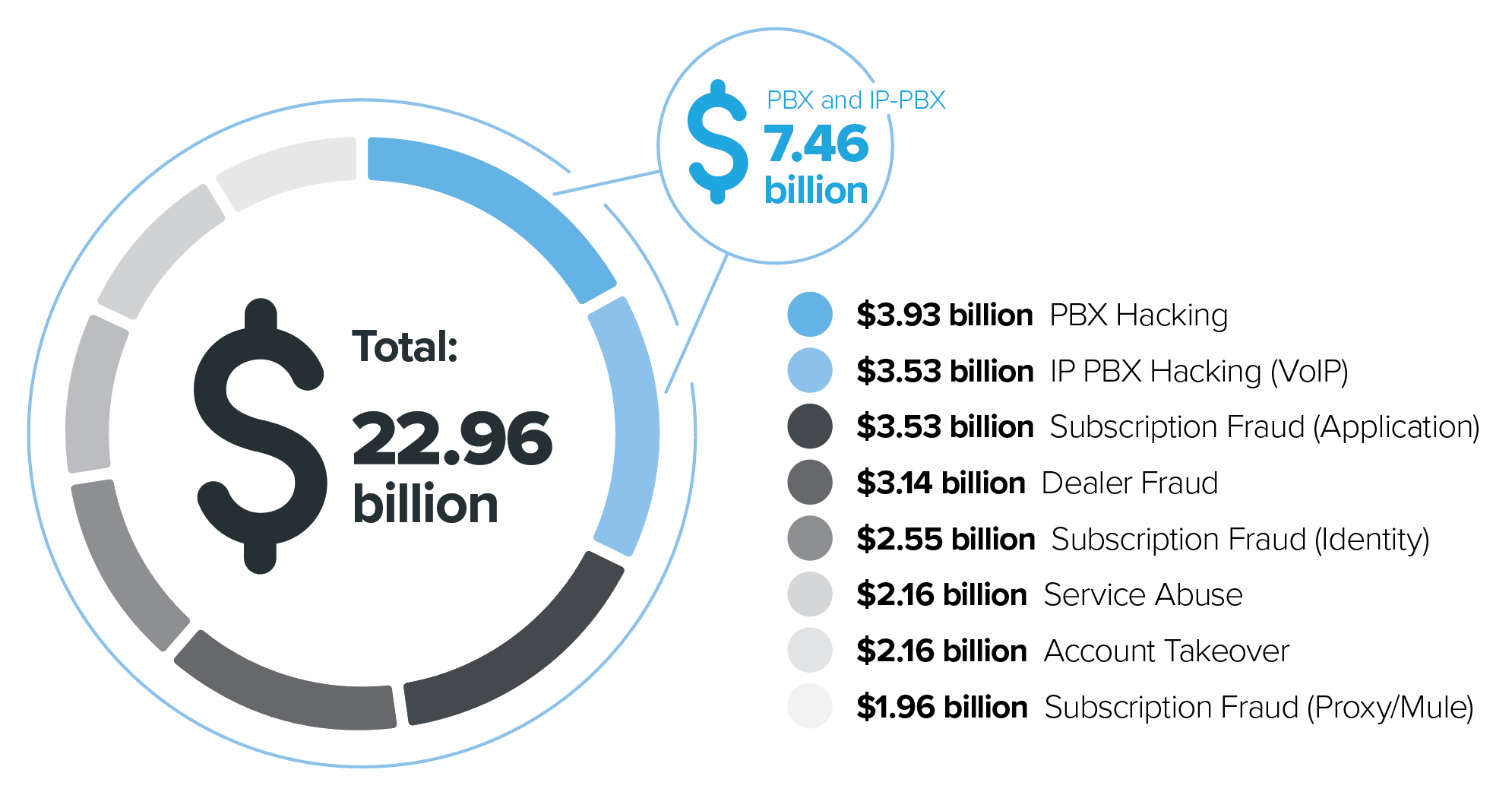
The Communications Fraud Control Association (CFCA), an industry organization on a mission to reduce fraud against carriers, conducts a bi-yearly Global Fraud Loss Survey. According to their latest survey, the telecommunications industry experienced $38.1 billion in fraudulent charges in 2016. What is concerning is that we know cyber fraudsters are continuously working to develop new and unusual ways to siphon money from well-known, established organizations of all shapes and sizes.
Here’s how the top fraud loss categories reported by operators in 2015 to the CFCA shook out:
- $3.93 billion – PBX (Private Branch eXchange) Hacking
- $3.53 billion – IP PBX Hacking (VoIP)
- $3.53 billion – Subscription Fraud (Application)
- $3.14 billion – Dealer Fraud
- $2.55 billion – Subscription Fraud (Identity)
- $2.16 billion – Service Abuse
- $2.16 billion – Account Takeover
- $1.96 billion – Subscription Fraud (Proxy/Mule)
The $7.46 billion in PBX and IP-PBX hacking is ground zero for fraudsters looking for vulnerable video conferencing systems to hack. Although PBX and VoIP PBX hacking were the top of the fraud loss categories reported by operators, there was another type of “hack” that continues to impact enterprises at an alarming rate while remaining under the radar.
The Top Security Vulnerabilities that Lead to Telecom Hacking
In the telecommunications world there are two very specific categories of hacking: user authentication hacking and SIP toll fraud hacking.
User Authentication Hacking
It was no surprise to see this type of hack at the top of the CFCA’s list. By using this tactic, hackers can gain full access to a PBX by simply uncovering vulnerabilities via network firewalls and enter through video edge devices. This process is most often accomplished via SIP trunking through VoIP PBX or via a direct gateway to the PSTN (e.g., ISDN gateway).
Once a hacker has access to a PBX or VoIP PBX system they can initiate calls, change call routing plans, and so on. By planning their attack over a weekend or in the early hours of the morning they can reduce their chances of detection and maximize their efforts. They quickly place an outrageous amount of long-distance calls and disappear leaving end-users with the bill. Interestingly, the other telecommunications hack-type didn’t make the CFCA’s list in 2015. However, we’re seeing that this hack can account for anywhere between 75%-90% of the total calls placed within larger organizations.
SIP Toll Fraud Hacking
SIP Toll Fraud should be a far more visible concern for IT teams. However, efforts by organizations to dodge negative press have created a vicious circle of vulnerability that pushes these risks into the shadows.
This hack type lives at the intersection of the video and voice world. SIP Toll Fraud can occur over PBX and VoIP PBX via video edge devices due to the flexibility and interoperability of the SIP, H.323, MS-SIP and other proprietary protocols used in the initiation of audio and video calls. These protocols allow for video and audio calls to be initiated from a registered or remote video/phone systems via poor video edge device dial plans and security settings.
Hackers specifically target call control edge devices and the internal connectivity to phone systems. To initiate an outbound phone call from the targeted video/audio network the hacker can ‘spoof’ a registration as an internal endpoint and then issue a series of dial attempts in the hopes of finding their way to your PBX via your dial plan. It is not strictly required to register as a local endpoint, but this may result in a higher level of call privileges and thus a higher degree of success in connecting outbound calls. In the case of internal registration, the device (or bot) would most commonly be registered to an ISDN or CUCM.
If a company has a long-standing or well known DNS record – they will be a target. This is precisely why large, enterprise organizations encounter such large instances of dial plan hacking (75%-90%). It also helps that enterprise organizations tend to have much deeper pockets than most, with the added benefit of being well-known brands that hackers can leverage to boost their notoriety.
SIP Security Vulnerabilities: How Hackers Exploit Video with Toll Fraud
Here’s how hackers perform SIP Toll Fraud:
Step #1: Hackers fish for potential victims by scanning service records (SRV records) for video-enabled web domains.
Step #2: Using video enabled domains found in the previous step, a hacker will direct a bot to attempt to place an audio call to a known phone number via the external video gatekeeper. The bot must use many different variations of the target number and attempts to connect an audio call by appending different likely phone prefixes used to direct audio calls to the phone network (one common prefixes is ‘91’ followed by the actual target number).
For example, let’s say that 999-345-6789 is a “good” phone number. The bot will be designed by hackers to dial the following series to hack the system:
- 01-999-345-6789
- 90-999-345-6789
- 91-999-345-6789
- 991-999-345-6789
- …etc.
Step #3: If any of the above dial strings results in a successfully connected call, then the hacker has immediately confirmed:
- Your phone network is indeed trunked to your video network.
- Determine what prefix is required to ensure that calls are properly routed to the phone provider.
- Actual ‘cash-in’ calls can now be triggered by leveraging items 1 and 2 (above) to complete their nefarious plan. This leaves companies on the hook for small, recurring phone charges or one, terrifying bill.
How To Discover and Take Action Against SIP Toll Fraud Probes with Vyopta
In an effort to take a stand against telecommunication security issues, providers like Vyopta are taking proactive measures to empower IT teams to identify and prevent SIP Toll calls by collecting, retaining, and searching Call Details Records (CDRs) from a network’s call controls and bridges. During Vyopta’s onboarding process, our team puts the right security precautions in place, such as preventing “audio only” calls made via video gateway devices from being hacked. From there, our intelligent algorithm will detect signaling as hackers continue to evolve and identify toll fraud.
Vyopta take a stand against telecommunication security threats – protecting your company’s network, and brand. Users easily access the exact data needed and share exactly how much of an impact their organizations security precautions have had or what breaches have occurred so teams can take action.
Even though network security is primarily every IT team members responsibility, it doesn’t stop there. In order for telecommunication security issues to be prevented and treated, everyone must play a role in protecting their network and brand. By implementing a proven solution like Vyopta in place, you’re arming your company to operate confidently, without the worry of being left on the hook for fraudulent charges or in the case of some companies, negative press.
Want to learn if your telecommunications network is truly protected from phone and video hacking or you’re paying hidden fees? Read the Vyopta White Paper: The $38 Billion Security Vulnerability Your Enterprise Cannot Afford to Ignore.