The Payment Card Industry’s Role in Unified Communication Compliance
Credit card and payment information passes through many different technologies these days, and the industry regulatory group known as PCI has expanded their Data Security Standard (PCI DSS) requirements to conventional communications systems, including endpoints and infrastructure. This rule went into effect on June 30, 2018, and those who don’t comply could face charges of up to $100,000 per month. It mostly affects companies banks and financial institutions. If you are affected, you are probably already aware. Today, we will show you how to use Vyopta and give you the information below to identify if you have any gaps in your coverage for PCI DSS requirements for TLS 1.1 or greater.
What is changing with new TLS PCI Compliances?
There have been several widely publicized vulnerabilities in both SSL and TLS security protocols that are widely used across many applications that transmit data over IP. This PCI DSS 3.2 update requires organizations to use the TLS 1.1 or new protocols (1.2 is “strongly recommended”) to patch the largest and most egregious vulnerabilities.
How does this apply to Unified Communications?
PCI DSS applies to any entity that stores, processes, or transmits cardholder data and/or sensitive authentication data. Since many transactions or interactions with customers now happen through phone or video conversations, that traverse through infrastructure, these conferencing endpoints, infrastructure, and phones fall under the PCI regulations.
How do I fix it?
In most cases, the fix is a simple software upgrade. In the cases of older phones and conferencing equipment that do not support HTTPS (and thus do not support TLS), you will need to replace them completely. For a list of firmware versions, consult these by vendor.
Cisco Firmware Versions that support TLS 1.1 and 1.2
Infrastructure:
CUCM, IM&P, uCXN,
PCD before 11.5.1(SU3)
Phones:
78xx/88xx 12.0
Software:
Jabber 10.7
Room/Desktop Endpoint Firmware
CE 9.1(3)
TC 7.3(11)
Cisco Hardware requiring upgrade:
– Older Immersive (TX and CTS devices)
– Legacy Phones (99xx, 89xx, 79xx, 69xx)
– VG202, VG204
– DX 650
Polycom – List not available.
Pexip – Not affected. All versions support TLS 1.1 or greater.
Zoom – Not Affected. All versions support TLS 1.1 or greater.
BlueJeans – Not Affected. All versions support TLS 1.1 or greater.
Microsoft Lync/Skype for Business Server – Default settings support TLS encryption of all traffic.
Updating your infrastructure is relatively simple; simply log in and check the firmware version and security settings to ensure TLS is enabled.
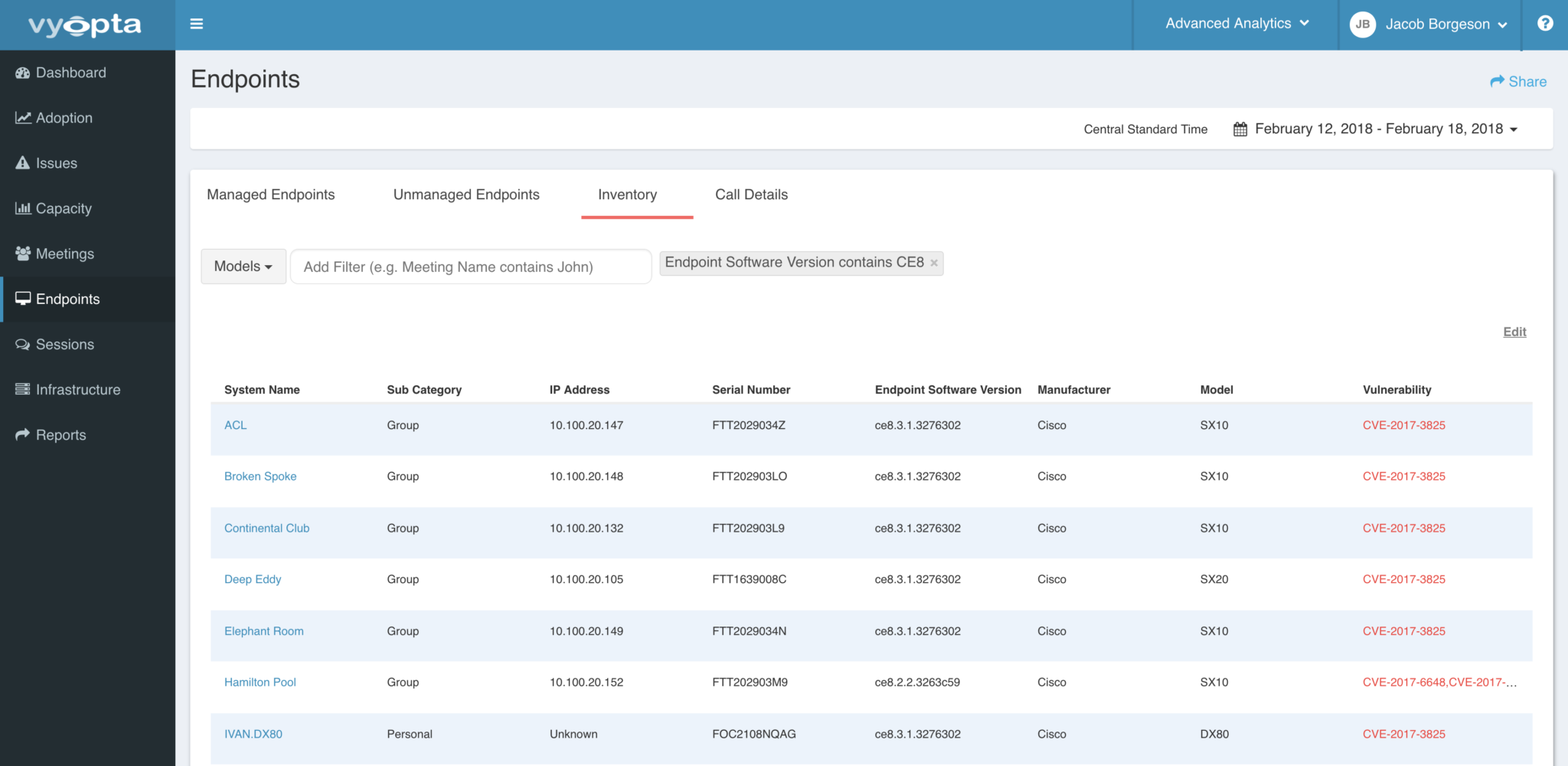
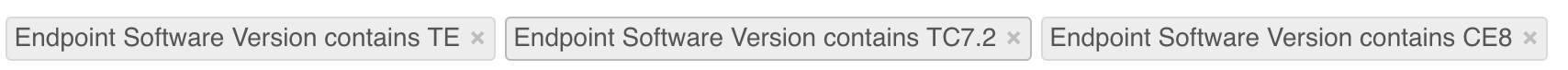
Endpoints can be trickier when you have hundreds out in the field. Vyopta can make it easy. Simply follow this link to the Endpoints tab. Once there, input these search terms –
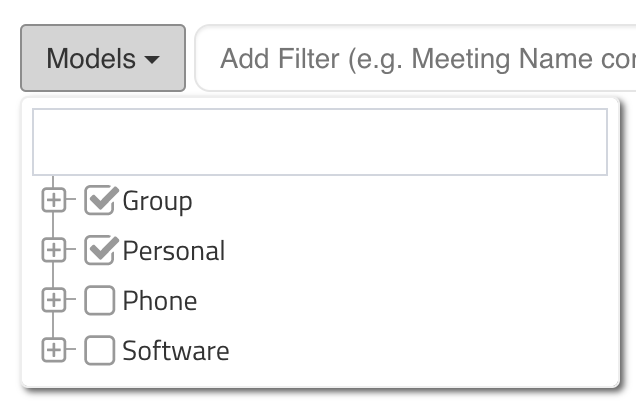
Each filter will need to be entered and executed independently. Once the results are displayed, the list can be addressed directly or exported to a CSV or Excel spreadsheet via the Share button at the top right. If you are accessing the endpoints on the page, you can click the endpoint and then click the management IP address to go through the normal update process for that endpoint.
If PCI DSS compliance for your UC environment is still a pain for you, then feel free to reach out to [email protected] for more info.